Curriculum
AppSec, Privacy & License Compliance
Introduction to AppSec
0/2Dependencies AppSec
0/5Code AppSec
0/2Runtime AppSec
0/2Dependencies License Compliance
0/2Privacy
0/2Quiz
0/1Bonus
0/3How SCA scanners work? How to read an SCA finding?
How do SCA scanners work?
SCA focuses on identifying and analyzing the third-party components used in an application. These components could be libraries, frameworks, or other external dependencies.
-
- Inventory Creation: The SCA tool first creates an inventory of all the third-party components used in the application. This is often done by scanning the application’s build files (e.g.,
pom.xmlfor Java Maven projects,package.jsonfor Node.js projects), package managers. SCA tools generate SBOMs. - Vulnerability Matching: The tool then compares the identified components and their versions against public vulnerability databases (like NVD) and other sources of security advisories.
- License Analysis: SCA tools identify licenses used by third-party components.
- Dependency Analysis: The tool analyzes the dependency tree to identify both direct and transitive dependencies. A transitive dependency is a dependency that is brought in by another dependency.
- Reporting: The SCA tool generates a report listing all the identified components, their versions, known vulnerabilities, license information, and dependency relationships.
- Inventory Creation: The SCA tool first creates an inventory of all the third-party components used in the application. This is often done by scanning the application’s build files (e.g.,
Who Decides It’s a Vulnerability?
SCA tools rely on public vulnerability databases (like the National Vulnerability Database – NVD) and security advisories from various sources. The SCA tool identifies the components in use and compares them against these databases. Again, human review is crucial to assess the real impact.
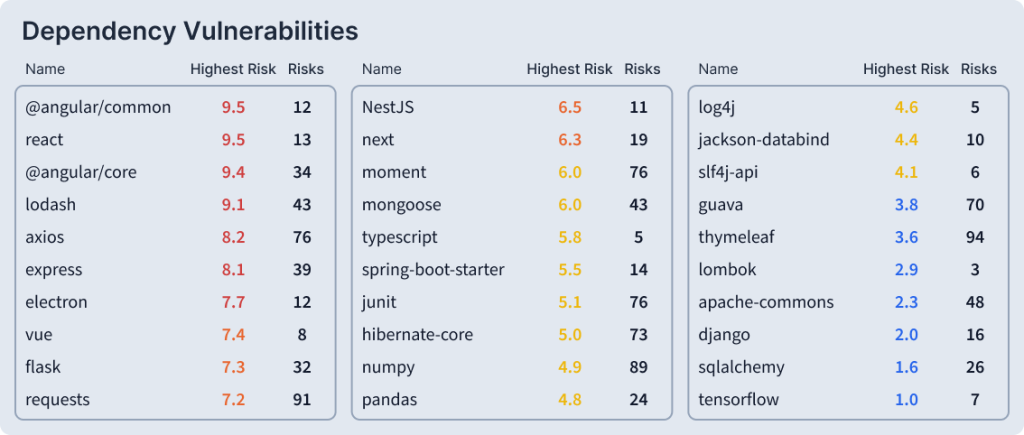
TLDR: So to put it simply, you have one super long list from NVD with every single vulnerability in components that exist, and another list of all your dependencies (Your SBOM), the SCA compares the two.
How to read an SCA finding?
SCA (Software Composition Analysis) tools scan your dependencies (open-source packages) for known vulnerabilities, licenses, and outdated components.
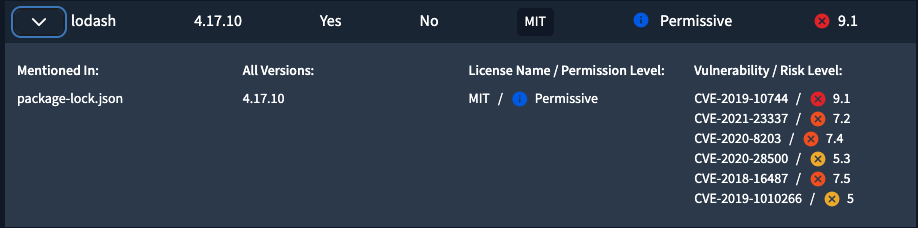
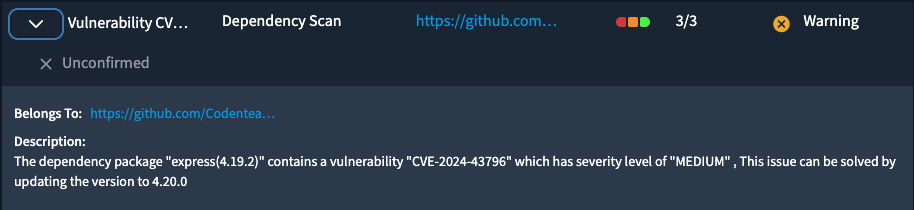
- Package Name & Version: Identifies the affected dependency and its version (e.g.,
log4j:2.14.1). - Vulnerability ID: Usually a
CVE(e.g.,CVE-2021-44228) or internal ID. - Severity: Often shown using CVSS scores or labels like Low, Medium, High, or Critical.
- Impact Description: Explains how the vulnerability can be exploited and what it affects (e.g., remote code execution).
- Fixed Version: The recommended version where the vulnerability is patched.
- Path to Dependency: Shows how the vulnerable package is included — direct or transitive.
- License Information: May flag non-compliant or risky licenses (e.g., GPL, AGPL, custom clauses).
Tip: Always prefer upgrading to a non-vulnerable version. Use dependency pinning to control what gets included.