Curriculum
AppSec, Privacy & License Compliance
Introduction to AppSec
0/2Dependencies AppSec
0/5Code AppSec
0/2Runtime AppSec
0/2Dependencies License Compliance
0/2Privacy
0/2Quiz
0/1Bonus
0/3How SAST scanners work? How to read an SAST finding?
How do SAST scanners work?
SAST tools work by parsing and analyzing the source code of an application without executing it. Here’s a simplified breakdown:
-
- Parsing: The SAST tool first parses the source code, breaking it down into an abstract syntax tree (AST) or another intermediate representation. This helps the tool understand the code’s structure and logic.
- Rule Application: The tool then applies its pre-defined rules to this parsed representation. These rules look for patterns that match known vulnerabilities. For example, a rule might look for instances where user-supplied data is directly used in a SQL query without proper sanitization (indicating a possible SQL injection vulnerability).
- Data Flow Analysis (Sometimes): Some SAST tools perform data flow analysis. This involves tracking how data moves through the application. This can help the tool identify vulnerabilities that are spread across multiple functions or files. For example, it might detect that user input from a form is passed to a database query function without being validated.
- Reporting: Finally, the tool generates a report listing all the potential vulnerabilities it has found, along with information about the location of the code, the severity of the potential vulnerability, and often remediation advice.
Some SAST use a form of regular expressions or string template matching to see if any line “looks” like a bad line.
Who Decides It’s a Vulnerability?
SAST tools rely on a predefined set of rules and patterns that are known to be associated with vulnerabilities. These rules are often based on industry standards like the OWASP Top 10, CWE (Common Weakness Enumeration), or SANS Top 25. The tool’s algorithms analyze the code against these rules. Human security experts ultimately decide if a finding is a real vulnerability (reducing false positives) and assess its severity.
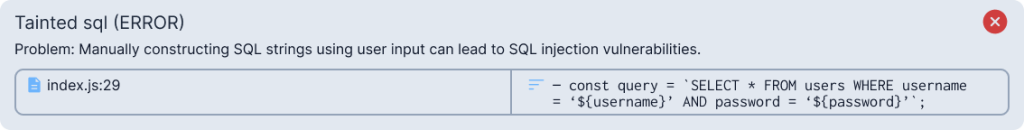
How to read an SAST finding?
As discussed in the previous lesson, SAST (Static Application Security Testing) tools analyze your source code to detect potential security vulnerabilities without executing the code. Each finding usually includes key components that help you understand and fix the issue.
- Issue Title: A short label for the vulnerability (e.g., “SQL Injection”, “Hardcoded Credentials”).
- Severity Level: Indicates how critical the issue is — usually labeled as Low, Medium, High, or Critical.
- File and Line Number: Tells you exactly where in the code the issue was found.
- Description: Explains why the issue matters, how it can be exploited, and what the risk is.
- Code Snippet: Highlights the vulnerable line or block of code.
- Remediation Guidance (Optional): Suggests how to fix or mitigate the issue (e.g., input validation, escaping output, removing secrets).
- CWE Reference (Optional): Common Weakness Enumeration ID that categorizes the issue (e.g.,
CWE-89for SQL Injection).
Tip: Prioritize high-severity findings that affect authentication, authorization, or user input. Look for false positives and verify findings before fixing.